Understanding the Shared Responsibility Model in Cloud Services
Successful cloud service utilization hinges on a trustworthy relationship between the customer and the cloud service provider (CSP). At WafaTech, we prioritize being a transparent security partner, which we consider fundamental to fostering customer trust. We are committed to guiding you on securing your products and safeguarding your customers' data.
You might think, "My product is hosted with WafaTech, so it's ready to deploy, right?" Not quite. While WafaTech plays a crucial role, we are not the sole custodians of the data you store on our services. The responsibility to protect your customers' data is shared among you, your customers, and WafaTech.
The Shared Responsibility Model (SRM) is a framework that specifies the division of responsibilities between the cloud service provider (in this case, WafaTech) and the customer (you) to secure the cloud environment. WafaTech is responsible for the security of your cloud instance—this includes physical security and the security of the virtualization services we offer. Conversely, you are responsible for the security within your cloud instance—this covers securing the operating system (OS) on your virtual machines and managing access to your instance.
The model applies differently across the three main types of cloud services:
1. Infrastructure as a Service (IaaS)
2. Platform as a Service (PaaS)
3. Software as a Service (SaaS)
Each service type involves a distinct allocation of responsibilities. Below is a graphic that illustrates the separation of responsibilities across these cloud service models:
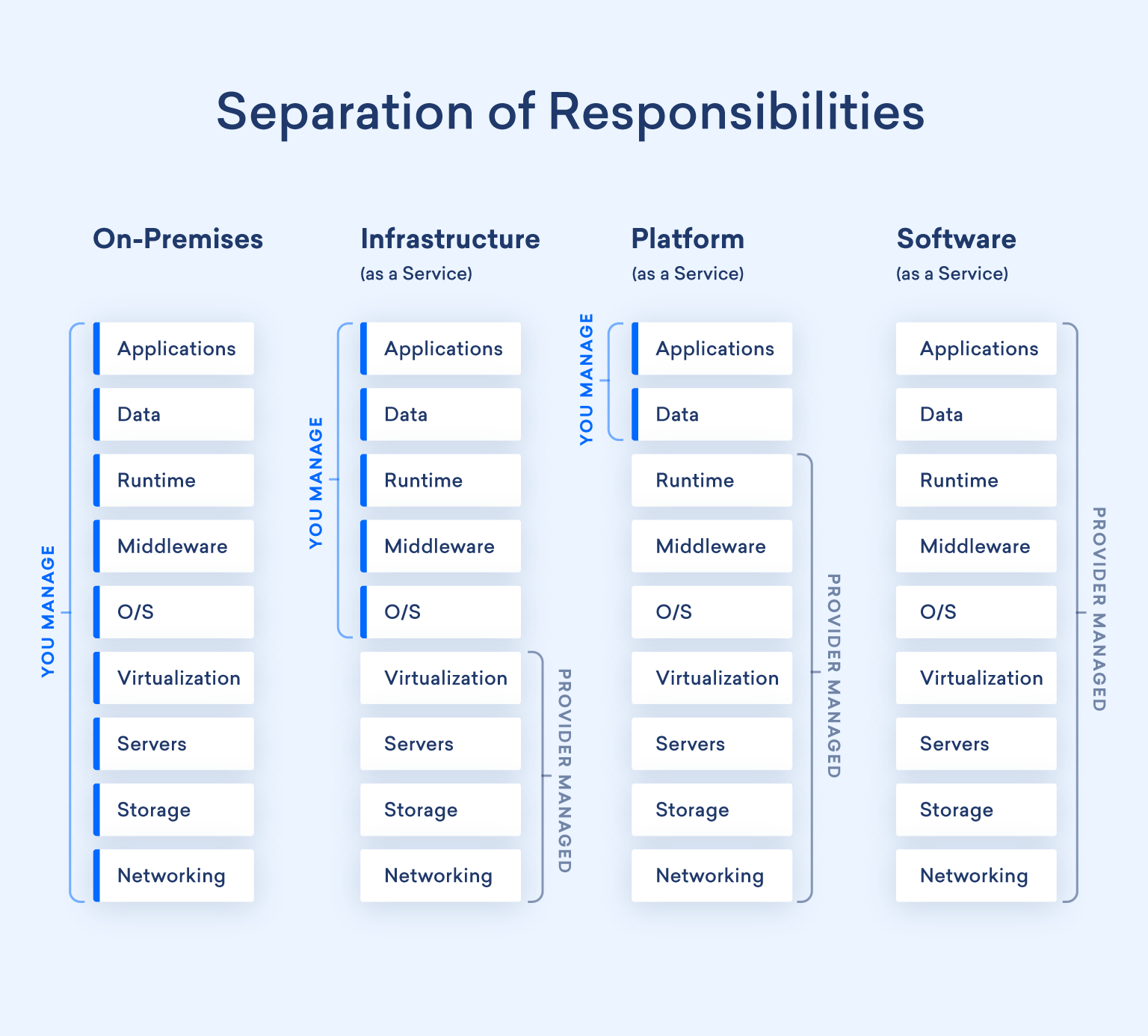
The Shared Responsibility Model (SRM) also encompasses IT controls, which are essential policies and procedures designed to meet standards, comply with regulations, and manage risks effectively. At WafaTech, we handle the physical and environmental controls, providing you with foundational protections you inherit from our services. Additionally, there are shared controls that both WafaTech and your company are responsible for, depending on the specific scenario. For instance, while WafaTech conducts internal security training, it is your responsibility to train your employees.
Moreover, there are controls that you are solely responsible for managing. A key example is identity and access management (IAM). For these areas, we recommend utilizing frameworks such as the NIST Cybersecurity Framework to identify and implement the specific controls needed.
Data protection involves multiple components and varies significantly based on your business requirements and the criticality of the data you store. Depending on these factors, your safeguards may differ from those needed by other companies.
We have developed these SRM guides to assist you in utilizing the safeguards available within our product line, aiming to enhance the protection of your business effectively.






